Cybersecurity for High-Net-Worth Connected Lifestyles: Beyond Traditional Home Security
The Unique Digital Risk Profile of Affluent Families
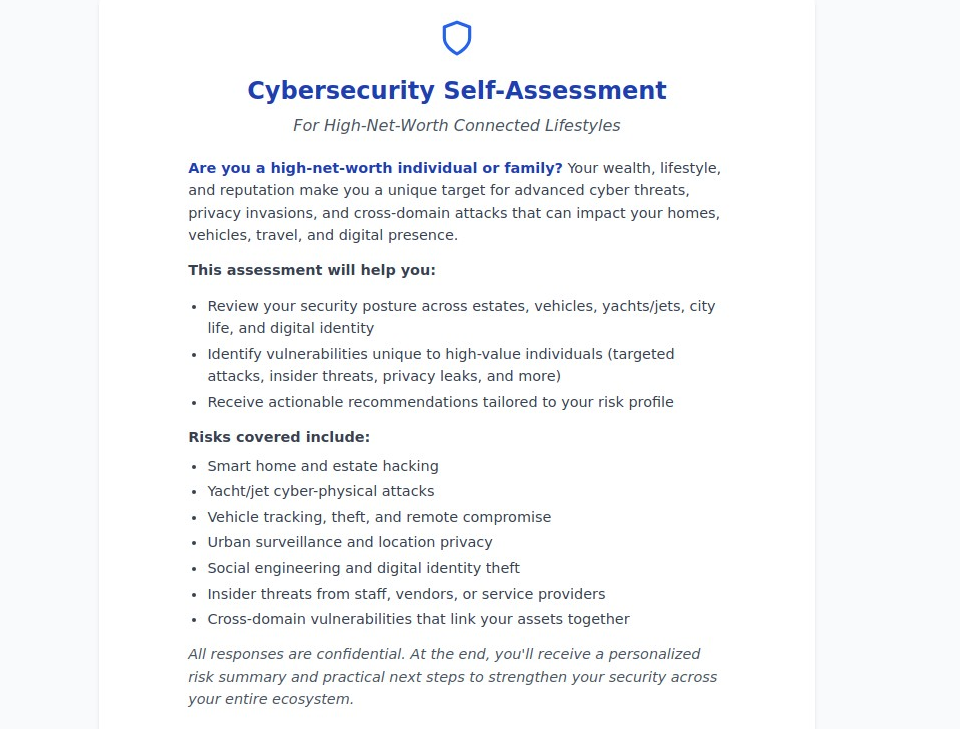
High-net-worth individuals and families face a fundamentally different cybersecurity landscape than the general population. Your wealth, lifestyle, and reputation create a unique target profile that requires specialized protection strategies extending far beyond traditional home security systems. When your digital ecosystem spans multiple estates, luxury vehicles, private aircraft, and urban interactions, standard cybersecurity approaches fall dangerously short.

Why Wealth Changes Everything in Cybersecurity
Advanced Persistent Threats Target High-Value Individuals
Cybercriminals increasingly view affluent families as high-value targets worth sustained, sophisticated attacks. Unlike opportunistic crimes affecting the general population, attacks against high-net-worth individuals often involve:
- Months of reconnaissance gathering intelligence on your lifestyle, travel patterns, and digital habits
- Multi-vector attacks simultaneously targeting your homes, vehicles, and digital presence
- Social engineering campaigns exploiting your public profile and family information
- Insider threat exploitation compromising staff, vendors, or service providers with access to your systems
- Cross-domain vulnerabilities where a breach in one area (like a smart car) provides access to others (like your home network)
The Connected Luxury Lifestyle Creates Unique Attack Surfaces
Your sophisticated lifestyle introduces cybersecurity challenges that don't exist for typical homeowners:
Multi-Property Complexity: Managing security across multiple estates, each with their own smart systems and staff access requirements.
Luxury Asset Integration: Private jets, yachts, and high-end vehicles contain sophisticated computer systems that can be remotely compromised.
Urban Privacy Challenges: Living and traveling in smart cities where ubiquitous surveillance requires active countermeasures for location privacy.
Service Provider Ecosystem: The numerous staff, vendors, and service providers supporting your lifestyle create multiple potential insider threat vectors.

The Five Critical Domains of High-Net-Worth Cybersecurity
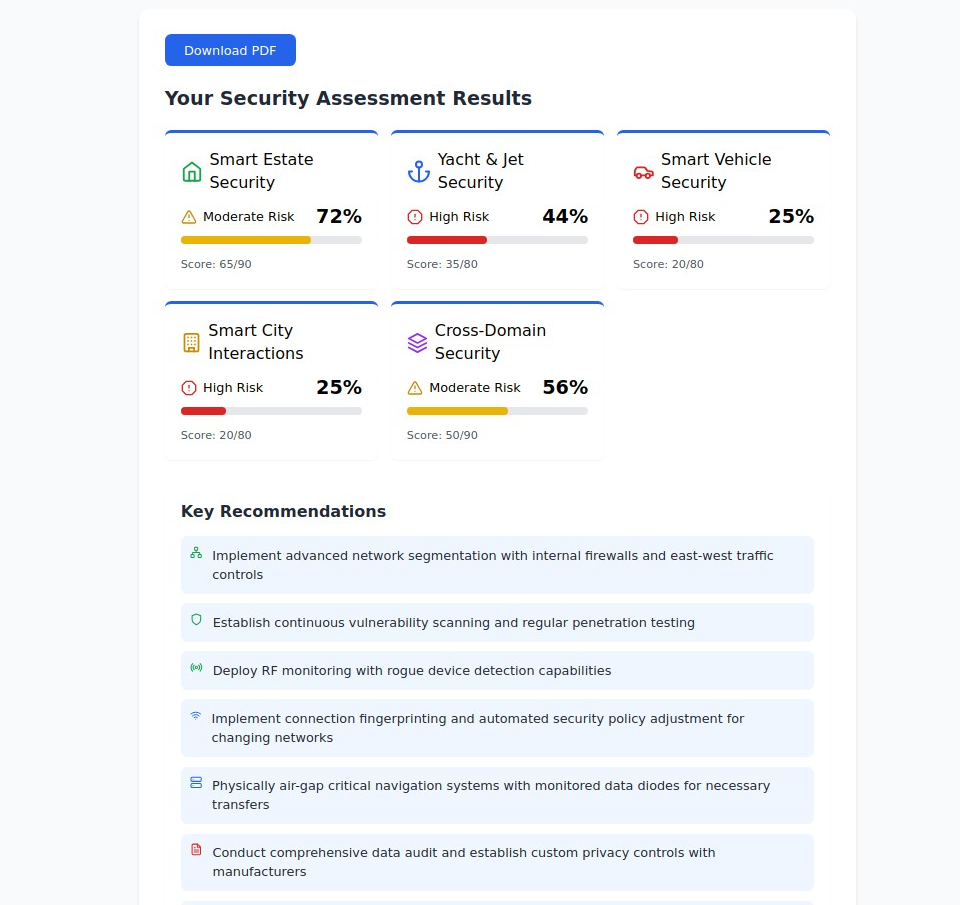
1. Smart Estate Security
Your primary and secondary residences likely contain dozens of connected devices, from security systems and climate controls to entertainment systems and smart appliances. Estate security goes beyond home automation to include:
- Network segmentation isolating critical systems from guest and staff access
- Advanced intrusion detection monitoring for both digital and physical threats
- Staff access management controlling which personnel can access different systems
- Vendor security requirements ensuring service providers meet your security standards
- Emergency isolation protocols quickly disconnecting compromised systems
2. Luxury Vehicle & Aircraft Security
Modern luxury vehicles and private aircraft are essentially computers with engines, containing hundreds of electronic control units connected to various networks. Key vulnerabilities include:
- Remote exploitation of vehicle systems through cellular, Wi-Fi, or Bluetooth connections
- Location tracking through various connected services and apps
- Physical access attacks when vehicles are serviced or parked in unsecured locations
- Navigation system compromise potentially affecting flight safety or travel security
- Data exfiltration from onboard entertainment and communication systems
3. Urban Interaction Privacy
High-net-worth individuals moving through smart cities face unique privacy challenges from ubiquitous surveillance systems. Critical considerations include:
- Facial recognition avoidance in public spaces and commercial areas
- Location pattern analysis that could reveal routine behaviors and vulnerabilities
- Social proximity tracking monitoring who you meet and where
- Digital payment tracing linking financial transactions to location and behavior data
- Communication interception in areas with sophisticated surveillance capabilities
4. Cross-Domain Security Integration
The greatest risks often emerge where your various digital assets intersect. Common cross-domain vulnerabilities:
- Shared credentials across multiple systems and properties
- Interconnected networks allowing lateral movement between estates, vehicles, and devices
- Unified management platforms that provide single points of failure
- Staff access overlap where personnel have access to multiple domains
- Data synchronization that can spread compromises across your entire digital ecosystem
5. Digital Identity & Privacy Protection
Your public profile and family information require active protection from both digital and physical threats. Essential protections include:
- Social media monitoring for information that could enable targeting
- Family member protection extending security to spouses and children
- Reputation management monitoring for false information or damaging content
- Financial privacy protecting transaction patterns and asset information
- Travel security maintaining operational security during domestic and international travel

Advanced Threats Targeting High-Net-Worth Individuals
Yacht and Jet Cyber-Physical Attacks
Modern luxury vessels and aircraft rely heavily on interconnected digital systems for navigation, communication, and operation. Attackers can potentially:
- Compromise navigation systems during critical operations
- Intercept communications revealing travel plans or business information
- Disable safety systems or create false emergencies
- Track movements for physical surveillance or planning attacks
Smart City Surveillance Exploitation
Urban environments with extensive IoT sensor networks create privacy risks through:
- Behavioral pattern analysis revealing routines and preferences
- Social network mapping identifying relationships and meeting patterns
- Predictive targeting using AI to anticipate your movements and activities
- Real-time tracking enabling physical surveillance or harassment
Insider Threat Amplification
The extensive staff and service provider ecosystem supporting affluent lifestyles creates numerous insider threat vectors:
- Privileged access abuse by domestic staff, drivers, or maintenance personnel
- Social engineering targeting of employees to gain system access
- Data theft opportunities from personnel with access to personal information
- Physical security bypasses using insider knowledge of security systems and routines
The Assessment Process: Comprehensive Risk Evaluation
Multi-Domain Analysis
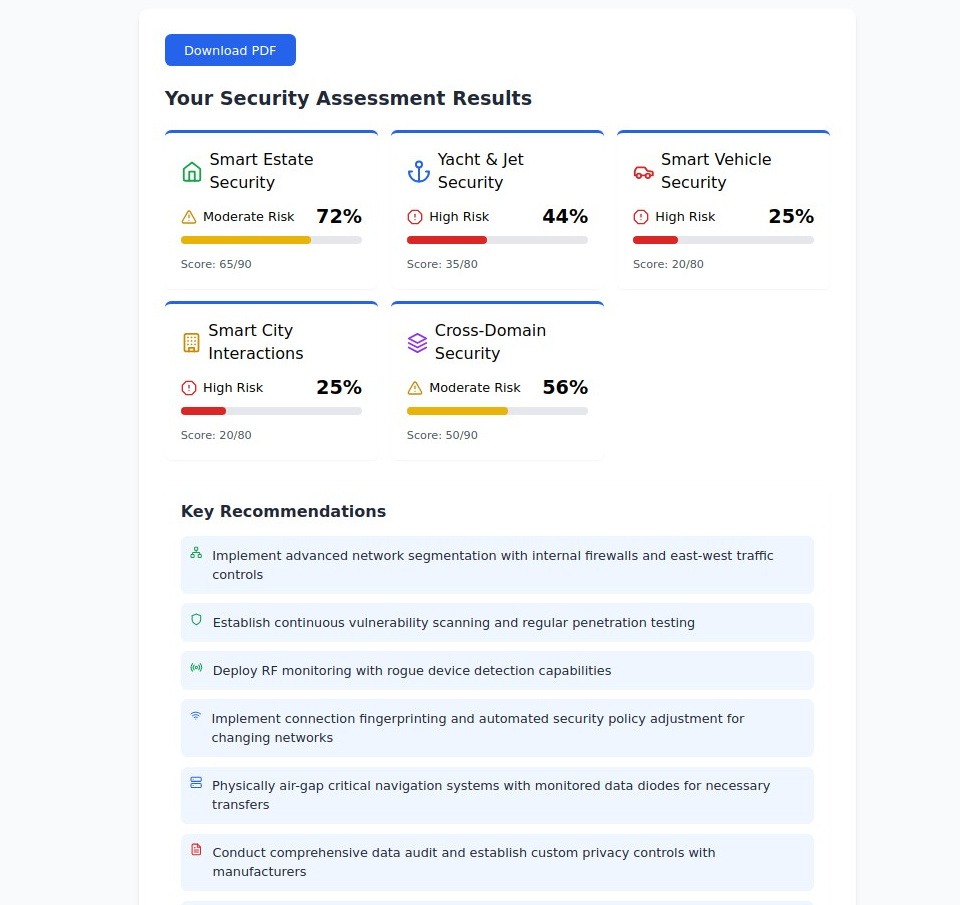
Our assessment evaluates your security posture across all five critical domains, providing specific risk scores and actionable recommendations for each area. The process examines:
- Current security implementations across all your properties and assets
- Vulnerability identification specific to high-value individual targeting
- Cross-domain risk assessment analyzing how different areas interact and create compound vulnerabilities
- Threat modeling based on your specific risk profile and lifestyle patterns
- Compliance evaluation ensuring adherence to relevant privacy and security regulations
Tailored Risk Profiling
Unlike generic cybersecurity assessments, our evaluation considers factors unique to high-net-worth individuals:
- Public visibility level and associated targeting risks
- Geographic risk factors based on primary and travel locations
- Asset complexity reflecting the sophistication of your connected ecosystem
- Staff and vendor ecosystem analyzing insider threat potential
- Regulatory requirements for financial privacy and international travel
Actionable Recommendations
Receive prioritized, implementable recommendations designed specifically for your lifestyle and risk profile:
- Technical implementations that work with luxury systems and aesthetics
- Operational procedures that integrate with existing staff and routines
- Vendor requirements for service providers and technology suppliers
- Family training programs ensuring all household members understand security practices
- Incident response planning tailored to high-net-worth individual needs
Implementation: Beyond the Assessment
Professional Security Integration
While our assessment provides crucial initial guidance, implementing comprehensive protection for high-net-worth lifestyles typically requires professional cybersecurity services specializing in affluent family protection. Key implementation considerations:
- Ongoing monitoring of your digital ecosystem for emerging threats
- Regular penetration testing to identify new vulnerabilities as systems evolve
- Incident response services providing immediate expert assistance during security events
- Threat intelligence specific to risks targeting high-net-worth individuals
- Privacy consulting for new technology adoption and lifestyle changes
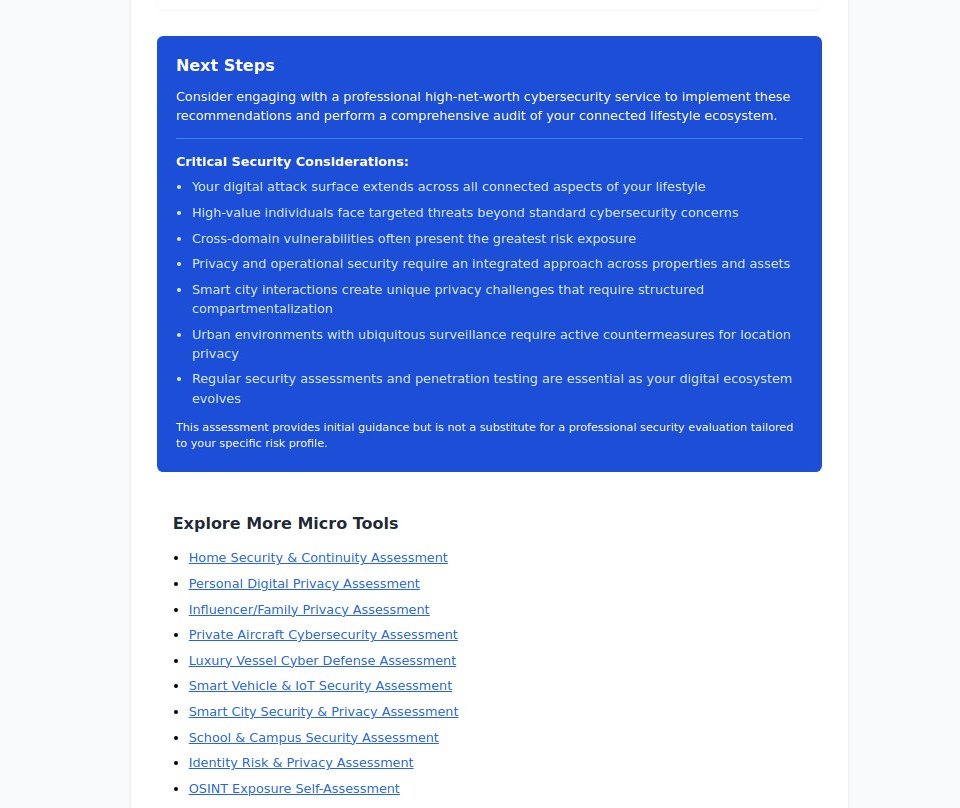
Critical Security Principles for Affluent Families
Assume You're a Target: High-net-worth individuals should operate under the assumption that sophisticated attackers are actively researching and targeting them.
Defense in Depth: Layer security measures across all domains rather than relying on single solutions.
Privacy by Design: Consider privacy implications before adopting new technologies or services.
Regular Assessment: Your digital ecosystem and risk profile evolve constantly, requiring periodic reassessment.
Professional Partnership: Complex high-net-worth cybersecurity typically requires ongoing professional support rather than one-time implementations.
Specialized Assessment Tools for Different Aspects of Your Lifestyle
Beyond our comprehensive lifestyle assessment, we offer specialized evaluations for specific high-net-worth security domains:
- Home Security & Continuity Assessment: Focused evaluation of primary and secondary residences
- Personal Digital Privacy Assessment: In-depth analysis of individual and family digital footprints
- Private Aircraft Cybersecurity Assessment: Specialized evaluation of aviation systems and travel security
- Luxury Vessel Cyber Defense Assessment: Comprehensive yacht and boat cybersecurity evaluation
- Smart Vehicle & IoT Security Assessment: Detailed analysis of connected automotive systems
- Smart City Security & Privacy Assessment: Urban interaction privacy and security evaluation
- Identity Risk & Privacy Assessment: Digital identity protection and reputation management
- OSINT Exposure Self-Assessment: Open source intelligence vulnerability evaluation
The Cost of Inadequate Protection
For high-net-worth individuals, cybersecurity failures can result in consequences far beyond typical data breaches:
- Financial theft through sophisticated fraud schemes
- Physical security compromise when digital breaches reveal travel plans or security measures
- Reputation damage from leaked private information or communications
- Family safety risks when children or spouses become targets
- Business disruption affecting professional activities and investments
- Privacy violations that permanently alter your lifestyle and freedom
Taking Action: Your Security Assessment
Understanding your current cybersecurity posture is the first step toward comprehensive protection. Our High-Net-Worth Cybersecurity Self-Assessment provides:
✓ Confidential evaluation of your multi-domain security posture ✓ Risk scoring across all five critical security domains
✓ Personalized recommendations tailored to your specific lifestyle and risk profile ✓ Implementation guidance for priority security improvements ✓ Professional service recommendations for comprehensive protection implementation
Your wealth, lifestyle, and reputation deserve protection as sophisticated as the threats targeting them.
Begin Your Confidential Assessment →
All responses are confidential. At the end, you'll receive a personalized risk summary and practical next steps to strengthen your security across your entire connected lifestyle ecosystem.