Smart Home Security & Continuity Assessment: Bringing Enterprise-Grade Protection to Your Household
Introduction
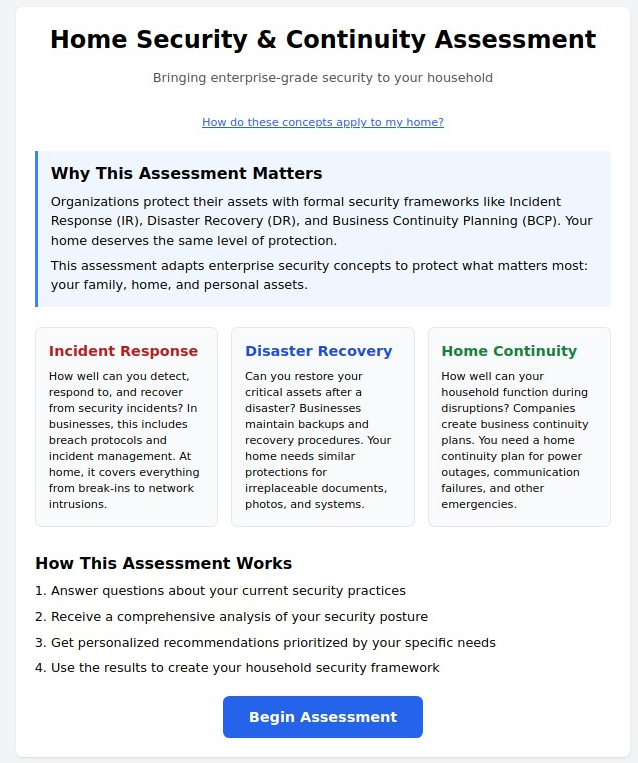
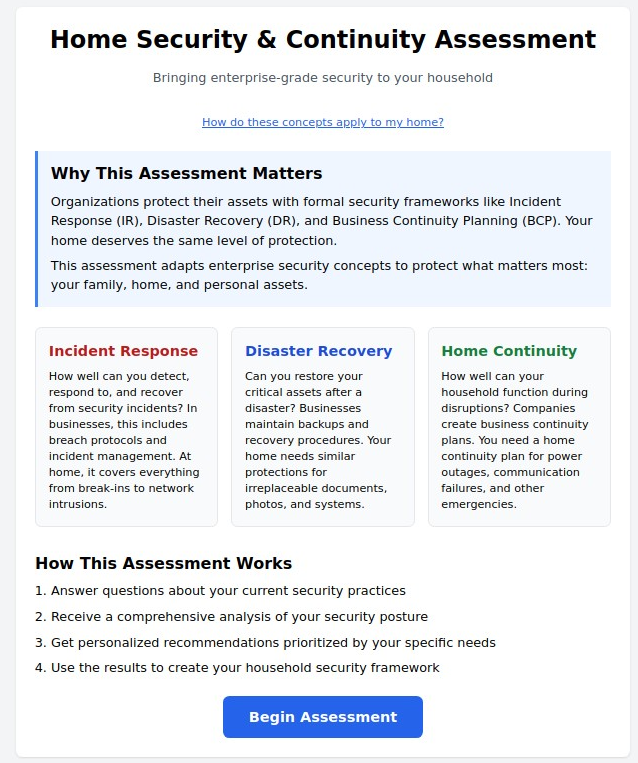
As our homes become increasingly connected through smart devices, IoT sensors, and automated systems, the need for structured security and continuity planning has never been greater. What was once reserved for Fortune 500 companies is now essential for protecting your family, property, and digital life. Our Smart Home Security & Continuity Assessment adapts proven enterprise frameworks to create a comprehensive protection strategy for your connected household.

Why Your Smart Home Needs Enterprise-Level Planning
The Modern Connected Home Reality
Today's smart homes contain dozens of connected devices—from security cameras and smart locks to voice assistants and automated lighting systems. Each device represents both a convenience and a potential vulnerability. A comprehensive assessment helps you understand and protect what matters most: your family's safety, privacy, and digital assets.
Beyond Traditional Home Security
While traditional home security focuses on physical protection, smart home security requires a holistic approach that addresses:
- Digital asset protection (photos, documents, personal data)
- IoT device vulnerabilities (smart cameras, thermostats, door locks)
- Network security (Wi-Fi, connected devices, remote access)
- Privacy protection (voice recordings, usage patterns, personal information)
- Service continuity (maintaining functionality during outages or failures)
The Three Pillars of Smart Home Protection
1. Incident Response (IR)
What it means for your home: Having a clear plan for security incidents affecting your smart home ecosystem.
Key components include:
- Asset Inventory: Knowing what connected devices and digital assets you need to protect
- Threat Recognition: Understanding potential risks from cyberattacks to physical break-ins
- Response Procedures: Having clear steps for immediate action during incidents
- Recovery Planning: Knowing how to restore security and functionality after an incident
Real-world scenarios:
- Smart security camera gets hacked and streams video publicly
- Wi-Fi network compromised, affecting all connected devices
- Smart lock malfunctions during a power outage
- Personal data stolen from a breached smart device
2. Disaster Recovery (DR)
What it means for your home: Ensuring you can restore critical systems and data after major disruptions.
Essential elements:
- Data Backup Strategy: Protecting family photos, important documents, and device configurations
- System Redundancy: Having backup methods for critical functions like security and communication
- Recovery Procedures: Step-by-step plans for restoring smart home functionality
- Alternative Access: Ensuring you can control your home even when primary systems fail
Disaster scenarios:
- Extended power outage affecting all smart devices
- Internet service disruption disabling cloud-connected systems
- Natural disaster damaging physical infrastructure
- Major cyberattack targeting IoT device manufacturers
3. Home Continuity Planning
What it means for your home: Maintaining essential household functions during various types of disruptions.
Planning considerations:
- Essential Services: Identifying which systems are critical for daily life
- Alternative Methods: Having non-digital backups for important functions
- Communication Plans: Ensuring family members can stay connected during emergencies
- Resource Management: Managing power, connectivity, and supplies during extended disruptions

How the Assessment Works
Step 1: Comprehensive Evaluation
The assessment examines your current smart home security practices across multiple dimensions:
- Device inventory and configuration
- Network security measures
- Data backup and recovery capabilities
- Incident response preparedness
- Physical and digital security integration
Step 2: Risk Analysis
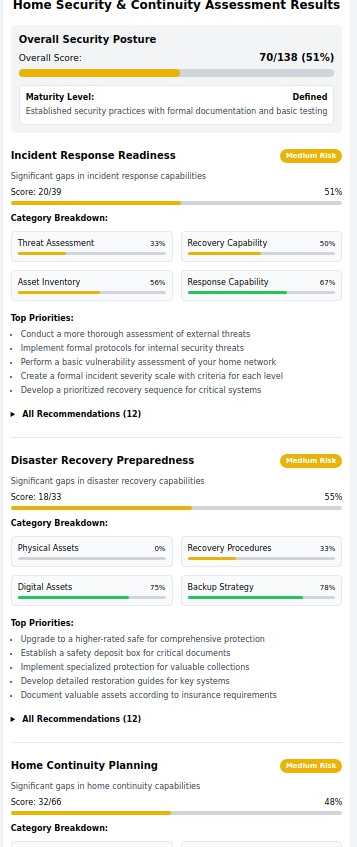
Receive a detailed analysis of your security posture, including:
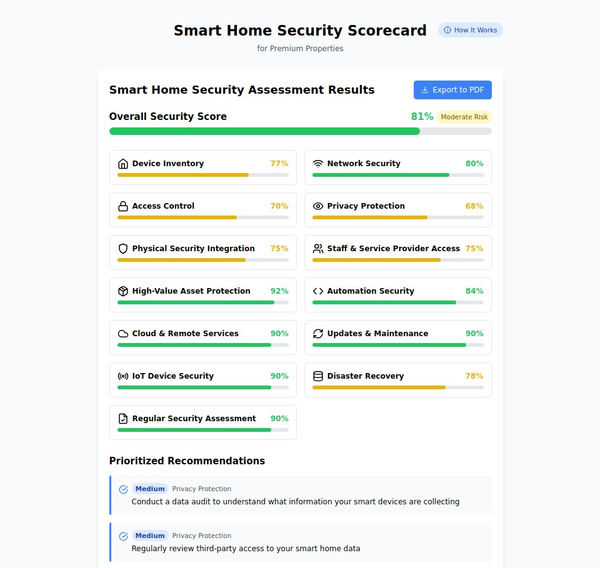
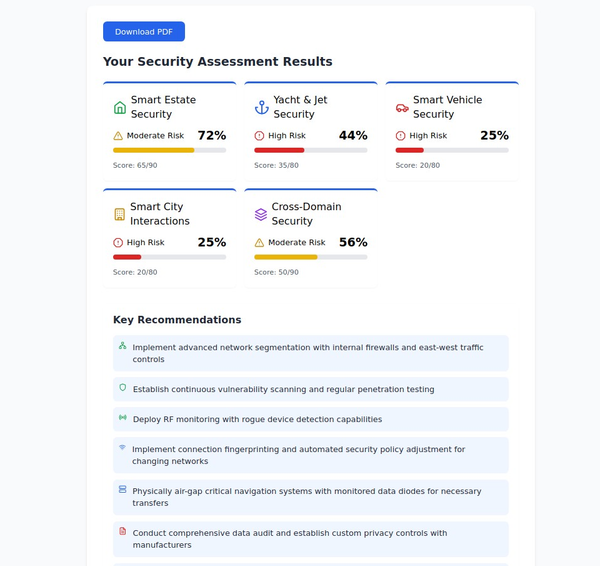
- Overall Security Score: Quantified assessment of your current protection level
- Category Breakdowns: Specific scores for different security domains
- Risk Identification: Highlighted vulnerabilities and gaps in protection
- Maturity Level Assessment: Understanding where you stand compared to best practices
Step 3: Prioritized Recommendations
Get actionable, prioritized recommendations tailored to your specific smart home setup:
- High-Impact Quick Wins: Easy improvements with significant security benefits
- Strategic Investments: Longer-term upgrades for comprehensive protection
- Step-by-Step Guidance: Clear instructions for implementing recommendations
- Resource Requirements: Understanding of time, cost, and technical complexity
Step 4: Implementation Framework
Use the results to build your household security framework:
- Security Policy Development: Creating family guidelines for device use and security
- Incident Response Procedures: Documented steps for common security scenarios
- Regular Review Schedule: Ongoing assessment and improvement processes
- Family Training: Ensuring all household members understand security practices
Smart Home-Specific Considerations
IoT Device Management
- Device Discovery: Cataloging all connected devices in your home
- Firmware Management: Keeping devices updated with latest security patches
- Network Segmentation: Isolating IoT devices from critical systems
- Default Credential Management: Changing default passwords and enabling strong authentication
Privacy Protection
- Data Collection Awareness: Understanding what data your devices collect and share
- Voice Assistant Security: Managing recordings and limiting access to sensitive information
- Camera and Sensor Placement: Balancing security needs with privacy expectations
- Third-Party Integrations: Controlling which services have access to your smart home data
Physical-Digital Integration
- Smart Lock Security: Ensuring backup access methods and monitoring for vulnerabilities
- Security System Integration: Coordinating traditional and smart security measures
- Power Backup Planning: Maintaining critical security functions during outages
- Physical Access Control: Managing who has access to smart home controls and devices

Assessment Benefits
Immediate Value
- Gap Identification: Discover unknown vulnerabilities in your smart home setup
- Risk Prioritization: Focus efforts on the most critical security improvements
- Cost-Effective Planning: Avoid expensive mistakes by following proven frameworks
- Family Safety: Enhance protection for your most valuable assets—your loved ones
Long-Term Advantages
- Scalable Security: Build a foundation that grows with your smart home expansion
- Insurance Benefits: Potentially reduce homeowner's insurance costs through documented security measures
- Property Value: Increase home value through professional-grade security implementation
- Peace of Mind: Confidence that your connected home is properly protected
Getting Started
Preparation Tips
- Device Inventory: List all connected devices in your home before beginning
- Network Documentation: Understand your home network setup and connected devices
- Family Input: Include all household members in security planning discussions
- Baseline Documentation: Take note of current security measures and concerns
Taking the Assessment
- Be Honest: Accurate responses lead to more valuable recommendations
- Think Holistically: Consider both digital and physical security aspects
- Document Everything: Keep records of your responses for future reference
- Plan for Implementation: Be prepared to act on the recommendations you receive
Conclusion
Smart home security isn't just about having the latest gadgets—it's about implementing a comprehensive strategy that protects your family, property, and digital life. By adapting enterprise-proven frameworks to residential use, our assessment helps you build a robust security posture that evolves with your connected home.
Take the first step toward enterprise-grade home protection. Complete your Smart Home Security & Continuity Assessment today and discover how to transform your connected house into a truly secure smart home.
Ready to begin? Start Your Assessment →
Your family's security is too important to leave to chance. Build the protection your connected home deserves.