The Growing Risk of Smart Home Hacks: How Safe Are Your Devices?

In the era of smart homes, where everything from doorbells to light bulbs is connected to the internet, convenience comes with a new level of risk. As more devices enter our homes, they create additional entry points for cyberattacks, putting personal data and even physical safety at risk. Over the past few years, several high-profile smart home vendors have been hacked, exposing vulnerabilities in both the technology and the security measures that protect it.

Smart home technology promises an easier, more connected life, but what happens when these connected devices become targets for hackers? In this article, we’ll explore the rising trend of smart home hacks, examine the major incidents that have impacted well-known vendors, and discuss how consumers can protect themselves in a world where privacy and security are under constant threat.
The Rise of Smart Home Technology — And the Risks
Smart homes are filled with devices designed to make life easier: video doorbells, smart locks, security cameras, thermostats, and even refrigerators connected to the internet. These devices collect and share vast amounts of personal data, often with minimal input from users. While the benefits are obvious—automation, remote control, and energy savings—this interconnectedness also makes homes more vulnerable to cyberattacks.
Hackers can exploit weak passwords, unpatched vulnerabilities, and poorly secured systems to gain access to personal data, control devices remotely, and even disable security systems. The impact of a smart home hack can be severe, ranging from data breaches to home invasions or privacy invasions.
A History of High-Profile Smart Home Hacks
To illustrate the scope of the problem, here are eight significant breaches and incidents that have affected major smart home vendors:Yes, several other smart home vendors have experienced security breaches in recent years, raising concerns about the security of connected devices and the personal data they handle. Here are some notable examples:
1. Ring (Amazon-owned)
In 2019, Ring, a popular smart home security company specializing in video doorbells and security cameras, faced a significant privacy scandal. Hackers gained access to multiple users' Ring cameras using stolen credentials. This led to several alarming incidents where hackers used the compromised cameras to harass users, including speaking to children through the devices. The breach was the result of weak password security, with many users reusing passwords across different platforms.
Lessons Learned:
- Ring quickly emphasized the need for multi-factor authentication (MFA) and stronger password policies.
- Users were advised to avoid reusing passwords and enable MFA for additional protection.
2. Nest (Google-owned)
Google-owned Nest has also been involved in security issues. In 2019, Nest users reported incidents where hackers took control of their cameras, thermostats, and other smart devices, broadcasting strange messages and controlling temperature settings. Like Ring, these breaches were not the result of a system-wide hack but were due to credential stuffing, where hackers used previously stolen usernames and passwords to gain access.
Lessons Learned:
- Nest urged customers to use unique, strong passwords and enable two-factor authentication to enhance security.
- Google also improved its security processes, encouraging the use of security alerts and enhanced privacy controls.
3. SimpliSafe
In 2019, it was discovered that SimpliSafe, another smart home security system provider, had vulnerabilities that allowed hackers to disarm the alarm systems using a simple radio-based replay attack. This was not the result of a data breach, but a security flaw that allowed an attacker to record and replay the disarm signal from the SimpliSafe keypad to the base station.
Lessons Learned:
- The incident prompted discussions about improving encryption and signal security for smart home devices, especially for alarm systems that could be compromised through radio frequency attacks.
4. Wink
In 2020, Wink, a company offering smart home hubs to control devices from multiple vendors, suffered an internal service disruption that left users unable to access or control their devices for an extended period. While this was not a direct hack, the company's poor communication and handling of the incident raised concerns about the security and reliability of cloud-connected smart home platforms.
Lessons Learned:
- The incident highlighted the risks associated with relying on cloud-based services for smart home devices, emphasizing the importance of transparency, robust backup systems, and local control capabilities for users.
5. ADT (Multiple Incidents)
Besides the recent ADT breaches in 2024, there was also a high-profile breach in 2020 where a rogue ADT employee in Texas gained unauthorized access to over 200 customer home security camera feeds. The employee added their personal email to customer accounts and watched live video feeds, raising concerns about insider threats and the need for stricter internal controls.
Lessons Learned:
- The incident underscored the importance of securing employee access to sensitive systems and conducting regular audits to detect unauthorized activity.
- ADT implemented additional security measures and auditing procedures after the breach.
6. Samsung SmartThings
In 2016, researchers uncovered vulnerabilities in Samsung’s SmartThings platform that allowed hackers to unlock doors and control other smart home devices. The security issues stemmed from design flaws in the platform’s authorization mechanisms, which allowed malicious third-party apps to exploit these vulnerabilities.
Lessons Learned:
- Samsung worked to patch the vulnerabilities and improve its API security, but the incident raised awareness about the potential dangers of third-party apps in smart home ecosystems.
7. TP-Link
In 2020, TP-Link smart home products were found to have vulnerabilities that could be exploited to control users' devices remotely. Security researchers discovered that attackers could take over smart plugs and light bulbs by exploiting weak default security settings and poorly implemented firmware updates.
Lessons Learned:
- TP-Link responded by rolling out security patches and encouraging users to regularly update their devices and change default passwords.
- The incident highlighted the need for stronger default security settings and regular firmware updates for IoT devices.
8. Vizio Smart TVs
In 2017, Vizio was fined by the Federal Trade Commission (FTC) for collecting data from its smart TVs without users’ knowledge or consent. Vizio had been tracking what users were watching and selling that data to advertisers. This incident didn’t involve a hack but demonstrated the privacy risks associated with smart devices and how companies handle user data.
Lessons Learned:
- Vizio agreed to pay a $2.2 million fine and change its data collection practices, emphasizing the importance of transparency in data collection and privacy policies for smart home devices.
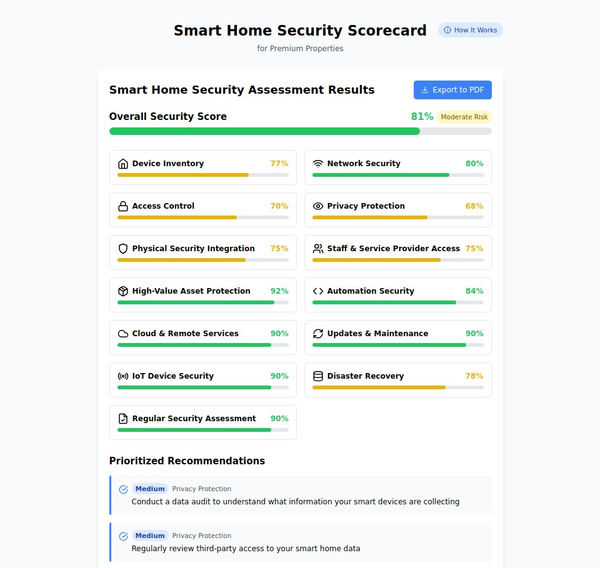
Key Takeaways for Smart Home Security:
- Credential Security: Many breaches occur due to weak or reused passwords, making it critical for both users and vendors to enforce strong password policies and enable multi-factor authentication.
- Privacy Concerns: Smart home devices often collect sensitive data, and users must be aware of how companies handle their data. Transparency in data collection and offering clear privacy settings is essential.
- Software and Firmware Updates: Regular updates to smart home devices are crucial to fix vulnerabilities that hackers can exploit.
- Local Control Options: As seen with the Wink outage, reliance on cloud-based services can sometimes leave users vulnerable. Offering local control options is one way to mitigate risks associated with cloud outages or breaches.
These incidents highlight the importance of strong security practices in the growing smart home industry, where privacy and security concerns remain at the forefront. For users, implementing best practices such as using strong passwords, enabling multi-factor authentication, and keeping devices up to date can go a long way in securing smart home ecosystems.What These Hacks Tell Us
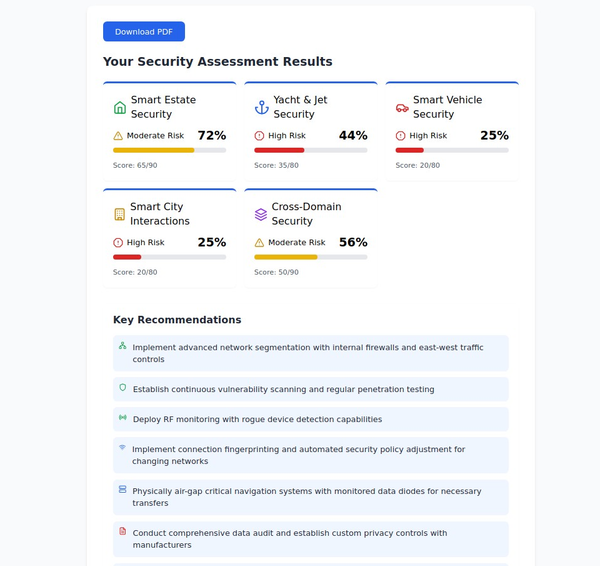
These incidents demonstrate several recurring themes in smart home security breaches:
- Weak Passwords: Many hacks, including those involving Ring and Nest, occurred because users reused passwords across multiple services. This made it easy for hackers to exploit credentials from other breaches and gain access to smart home devices.
- Lack of Two-Factor Authentication (2FA): Many of the affected vendors did not initially require or strongly promote 2FA, making it easier for attackers to take over accounts with just a stolen password. Enabling 2FA adds an extra layer of security that can prevent unauthorized access, even if the password is compromised.
- Insecure Default Settings: Some smart home devices, such as those from TP-Link, shipped with weak security settings or were not updated regularly with security patches. This allowed attackers to exploit known vulnerabilities that had not been fixed.
- Insider Threats: The ADT incident highlighted the risks of insider threats, where employees with access to sensitive systems abuse their privileges. Companies need to enforce stricter controls, including regular audits and access reviews, to prevent unauthorized access.
- Reliance on Cloud Services: The Wink outage demonstrated how reliance on cloud services can create points of failure. When servers go down, users lose access to their devices, underscoring the importance of local control options for critical systems like security.
Protecting Your Smart Home
While these breaches are alarming, there are steps you can take to protect your smart home devices from hackers:
- Use Strong, Unique Passwords: Avoid reusing passwords across different accounts. Use a password manager to create strong, unique passwords for each device or service you use.
- Enable Two-Factor Authentication (2FA): Wherever possible, enable 2FA to add an extra layer of security to your accounts. This ensures that even if your password is stolen, a hacker cannot easily access your account.
- Update Firmware Regularly: Smart devices often receive firmware updates to patch security vulnerabilities. Ensure that your devices are set to automatically update or check for updates regularly.
- Monitor Your Devices: Keep an eye on your smart home devices for unusual behavior, such as unexpected reboots or strange activity in your network logs. If something seems off, investigate immediately and change your credentials.
- Use Local Control Where Possible: Some smart devices offer the option to operate without relying on the cloud. Whenever possible, opt for local control to reduce the risk of outages or breaches impacting your devices.
- Limit Data Sharing: Be mindful of what data your smart home devices collect and share. Review privacy settings and turn off data collection where it isn’t necessary for the device’s functionality.
Conclusion
The convenience of smart homes comes with significant security risks that must be carefully managed. As smart home devices become more prevalent, the potential for hacks and data breaches grows. By taking proactive steps to secure your devices—using strong passwords, enabling two-factor authentication, and keeping devices updated—you can reduce the chances of falling victim to a smart home breach.
Smart home security should be a priority for both manufacturers and consumers. Vendors need to prioritize robust security measures, and users need to take an active role in securing their connected devices to protect their homes and personal data in this increasingly digital age.